The payment industry stands at a dangerous crossroads. While enterprise leaders celebrate the rapid adoption of embedded finance and real-time payment rails, a more troubling reality emerges from iMali’s latest research: the very APIs powering these innovations have become the most exploited attack vectors in payment fraud history, causing an Online Payment Security Crisis.
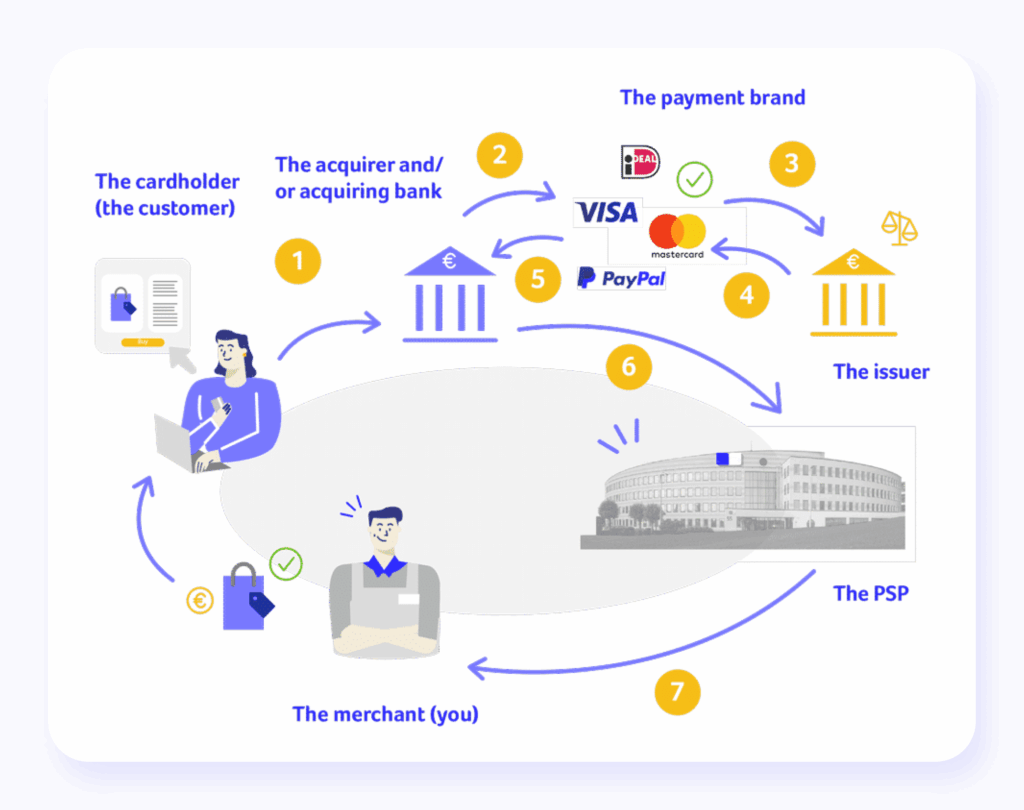
Our comprehensive analysis of payment security incidents throughout 2025 reveals a startling truth that contradicts conventional wisdom about payment protection. The greatest threats aren’t coming from external hackers using sophisticated zero-day exploits; they’re emerging from authenticated sessions, trusted third-party integrations, and the embedded finance APIs that enterprises rely on for competitive advantage.
The Authentication Paradox
When Security Becomes the Vulnerability
Traditional payment security focused on perimeter defense: strong authentication, secure channels, and encrypted transmission. Yet iMali’s fraud intelligence data shows that 95% of successful payment attacks in 2025 originated from authenticated sessions. This represents a fundamental shift that challenges every assumption about payment security architecture.
The authentication paradox reveals itself most clearly in embedded finance implementations. When payment capabilities are embedded within non-financial platforms from e-commerce sites to ride-sharing apps, the attack surface expands exponentially. Each integration point becomes a potential vulnerability, yet most enterprises continue applying traditional security models designed for centralized payment processing.
Consider the implications: a customer successfully authenticates with their payment credentials, passes all fraud detection checks, and initiates what appears to be a legitimate transaction. However, the underlying API infrastructure interprets the request differently than intended, allowing attackers to manipulate payment amounts, redirect funds, or access sensitive financial data. This isn’t theoretical; it’s happening across enterprise payment systems daily.
The root cause lies in how authentication systems handle distributed payment architectures. Legacy fraud detection tools evaluate individual transactions but lack visibility into the complex API chains that process embedded payments. When a payment request moves through multiple API endpoints, from the merchant platform to payment processors to banking systems, each handoff creates opportunities for manipulation that traditional monitoring cannot detect.
The Embedded Finance Security Illusion
Embedded finance promised to revolutionize customer experience by seamlessly integrating payment capabilities into digital platforms. The $250 billion market projection attracted massive enterprise investment, but iMali’s research reveals a troubling security reality that most organizations haven’t acknowledged.
The embedded finance security model relies on a distributed trust framework where multiple parties share responsibility for protecting customer data and transaction integrity. However, our analysis of security incidents shows that this distributed approach creates accountability gaps that attackers exploit systematically.
When a ride-sharing app embeds payment processing, customer financial data flows through the app provider’s systems, multiple API providers, payment processors, and banking infrastructure. Each entity implements different security standards, monitoring capabilities, and incident response procedures. The result is a security framework that’s only as strong as its weakest link, and that link is often invisible to the enterprise that owns the customer relationship.
The complexity becomes even more problematic when considering fourth and fifth-party vendor relationships. Many embedded finance providers rely on subcontractors for specific API functions, creating extended vendor chains that most enterprises never evaluate for security risks. Our research identified cases where payment fraud originated from compromised APIs operated by vendors that the primary enterprise had never directly assessed.
This distributed risk model fundamentally contradicts traditional enterprise security governance. Most organizations have sophisticated processes for evaluating direct vendors but lack frameworks for assessing the extended vendor networks that support embedded finance integrations. The result is payment security exposure that’s both extensive and largely invisible to enterprise risk management.
The Real-Time Compliance Trap
The push toward real-time payments created another unexpected security vulnerability. As payment rails achieve near-instantaneous settlement, the traditional window for fraud detection and transaction reversal essentially disappears. This shift demands fundamentally different security approaches, yet most enterprises continue using detection systems designed for batch-processed payments.
Real-time payment security requires predictive fraud prevention rather than reactive detection. Traditional systems identify suspicious patterns after transactions are complete, enabling chargebacks and reversals. However, real-time settlements create irreversible payment flows where post-transaction fraud detection becomes ineffective recovery rather than prevention.
The compliance implications are equally challenging. Cross-border real-time payments must satisfy anti-money laundering (AML) and counter-terrorism financing (CTF) requirements across multiple jurisdictions simultaneously. Our research found that many real-time payment implementations lack adequate compliance automation, creating regulatory exposure that grows with transaction velocity.
The regulatory complexity multiplies when considering data privacy requirements. Real-time cross-border payments often involve customer data flowing through multiple jurisdictions with different privacy regulations. GDPR requirements may conflict with AML data retention mandates, while real-time processing timelines leave insufficient opportunity for manual compliance review.
Enterprise payment leaders face an impossible choice: embrace real-time payment capabilities that customers demand while accepting security and compliance risks that traditional frameworks cannot address adequately. This tension explains why many large enterprises continue relying on slower payment methods despite competitive pressure to adopt real-time alternatives.
API Security
The Overlooked Foundation
While payment security discussions typically focus on fraud detection algorithms and customer authentication, iMali’s research identifies API security as the most critical and most neglected component of payment protection. The proliferation of payment APIs has created attack surfaces that most enterprises neither understand nor monitor effectively.
Payment API vulnerabilities manifest in several forms that traditional security tools miss entirely. Server-side request forgery (SSRF) attacks enable manipulation of API calls to redirect payments or access unauthorized data. Broken object-level authorization allows authenticated users to access payment information beyond their permitted scope. These vulnerabilities exist within the API infrastructure itself, making them invisible to transaction-level fraud detection.
The challenge intensifies with the widespread adoption of third-party payment APIs. Most enterprises integrate multiple payment providers to optimize conversion rates and reduce geographic restrictions. However, each API integration introduces unique security considerations that require specialized evaluation. A vulnerability in one payment API can compromise the entire payment infrastructure, yet most enterprises lack the expertise to assess API security comprehensively.
API security becomes even more complex when considering the development lifecycle. Payment APIs evolve continuously as providers add features, fix bugs, and respond to security threats. These updates can introduce new vulnerabilities or change security assumptions in ways that break existing protections. Our research found numerous cases where routine API updates inadvertently created security gaps that attackers exploited before enterprises recognized the exposure.
The solution requires treating API security as a distinct discipline rather than a subset of general application security. Payment APIs handle sensitive financial data and enable irreversible transactions, creating risk profiles that demand specialized security approaches. This includes comprehensive API testing, continuous vulnerability monitoring, and security frameworks designed specifically for payment API architectures.
Cross-Border Complexity
Where Regulation Meets Reality
Cross-border payments represent the most complex intersection of security, compliance, and operational challenges in the payment ecosystem. iMali’s analysis reveals that regulatory complexity, rather than technical limitations, has become the primary barrier to secure cross-border payment innovation.
The compliance burden for cross-border payments has increased exponentially as regulators attempt to address money laundering, terrorism financing, and tax evasion. Each jurisdiction maintains distinct requirements for transaction reporting, customer identification, and suspicious activity monitoring. Financial institutions must simultaneously satisfy multiple regulatory frameworks while maintaining competitive transaction processing speeds.
This regulatory complexity creates security vulnerabilities that attackers exploit systematically. Compliance systems designed for one jurisdiction may lack visibility into requirements for other markets, creating gaps in monitoring and reporting. Our research identified cases where criminals exploited these regulatory blind spots to move illicit funds through legitimate cross-border payment channels.
The situation becomes more problematic when considering emerging payment technologies. Blockchain-based cross-border payments, stablecoins, and central bank digital currencies (CBDCs) operate under evolving regulatory frameworks that lack comprehensive security guidelines. Enterprise payment teams must implement these technologies while navigating uncertain compliance requirements and minimal security precedents.
The regulatory uncertainty particularly affects smaller enterprises seeking to expand internationally. Large financial institutions have compliance teams capable of navigating complex regulatory requirements, but smaller companies often lack the expertise to assess cross-border payment risks adequately. This creates a two-tier market where regulatory complexity becomes a competitive barrier rather than a protection mechanism.
The Intelligence Gap
Why Traditional Monitoring Fails
Current payment security monitoring relies heavily on transaction pattern analysis and customer behavior modeling. However, iMali’s research demonstrates that these approaches fail to address the sophisticated threats targeting modern payment infrastructure.
Traditional fraud detection analyzes individual transactions or customer behavior patterns but lacks visibility into the underlying infrastructure that processes payments. When attackers compromise API endpoints, manipulate payment routing, or exploit integration vulnerabilities, transaction-level monitoring does not indicate the compromise. The attack remains invisible until significant financial losses accumulate.
The monitoring gap becomes particularly problematic with embedded finance implementations. Customer behavior appears normal from the perspective of transaction monitoring, while attackers manipulate the underlying payment infrastructure to redirect funds or harvest financial data. This infrastructure-level compromise can persist for months without detection using traditional monitoring approaches.
Effective payment security requires infrastructure intelligence that complements transaction monitoring. This includes real-time API behavior analysis, payment routing verification, and continuous assessment of third-party integrations. However, most enterprises lack the technical capabilities or security expertise to implement comprehensive infrastructure monitoring.
Building Resilient Payment Intelligence
The evolution of payment fraud demands a corresponding evolution in security intelligence. Traditional reactive approaches that identify threats after compromise must be supplemented with predictive intelligence that prevents attacks before they succeed.
Effective payment intelligence requires comprehensive visibility across the entire payment ecosystem, from customer authentication through final settlement. This includes monitoring API behavior, analyzing payment routing patterns, and evaluating third-party integration security continuously. The intelligence must operate in real-time to address the instant settlement characteristics of modern payment systems.
The technical requirements for payment intelligence extend beyond traditional security tools. Payment-specific threat detection requires understanding legitimate payment flows, normal API behavior patterns, and typical customer transaction characteristics. Generic security monitoring tools lack the domain expertise necessary for effective payment fraud prevention.
Implementation of comprehensive payment intelligence also requires organizational changes. Traditional security teams often lack payment domain expertise, while payment operations teams may not understand advanced security threats. Effective payment security requires cross-functional teams that combine payment expertise with security intelligence capabilities.
The Path Forward
Redefining Payment Security
The payment security challenges of 2025 require fundamental changes in how enterprises approach fraud prevention and risk management. Traditional perimeter-based security models must evolve into comprehensive intelligence frameworks that address distributed payment architectures and real-time processing requirements.
Success requires treating payment security as a strategic business capability rather than a technical compliance requirement. This includes investing in payment-specific security expertise, implementing comprehensive API monitoring, and developing incident response procedures designed for real-time payment environments.
Enterprise payment leaders must also recognize that security and innovation are not opposing forces. Properly implemented payment intelligence enables safe adoption of emerging technologies while providing competitive advantages through superior fraud prevention and customer experience.
The organizations that successfully navigate this transition will establish significant competitive advantages through superior payment security capabilities. Those that continue relying on traditional approaches will face increasing fraud losses, regulatory exposure, and customer trust issues that undermine their payment strategies.
The payment security revolution has begun. The question is whether enterprises will lead the transformation or become casualties of their failure to adapt.
This analysis is based on iMali’s proprietary research into payment security trends and enterprise fraud prevention strategies. For detailed implementation guidance and access to our payment intelligence APIs, contact our enterprise team.